Why the race to deliver products faster could be hampering product security
The total number of IoT malware attacks passed 57 million in the first half of 2022, but are organisations and connected device users truly aware of the threat to their security and privacy? Here’s a deeper look at whether the race to rush digital products to market is hampering security and what governments and organisations are doing about it.

According to the IDC’s Worldwide Digital Transformation Spending Guide, worldwide direct digital transformation investments are set to grow at a five-year CAGR of 16.3 per cent. This will translate to a whopping $3.4 trillion investment in 2026 alone.
One of the big reasons for this is the fact that digital transformation can contribute hugely to shortening a product’s time to market. In fact, it’s a core motivation behind many digital transformation strategies: a shorter time to market for a connected product improves customer satisfaction, helps gain competitive advantage and makes the delivery process more streamlined.
For manufacturers of IoT-enabled devices, a shorter time to market is crucial considering the sheer demand for IoT products (about two billion devices sold globally every year) and stiff competition among sellers. The McKinsey Global Institute estimates that IoT has the potential to generate $4 trillion to $11.1 trillion in economic value by 2025. There is significant demand for use cases such as inter-machine communication, machine-to-infrastructure communication, asset tracking, remote security and access control, home and industrial building automation and more.
There is evidence that investing in disruptive technologies and embracing innovation can deliver measurable outcomes here. According to Cognizant, investments in cutting-edge product engineering, data, development, digital engineering and quality assurance can enable companies to reduce time to market by up to 50 per cent and double annual revenue in just two years.
With globalisation enabling businesses to rival their offshore peers to grab a share of the global consumer market, the competition to deliver better and more affordable products, ensure round-the-clock customer service, and build deeper relationships with customers has never been tougher. These factors make shorter time to market crucial for business continuity, forcing businesses to adopt cutting-edge product development methodologies, such as Agile, to build products better and ensure faster deliveries.
See more: The electronic security industry is changing – Evolution leads the way
Product quality, not product security, rule the roost
The race to rush products and applications quicker to market has given rise to the concept of Agile product development, where companies apply Agile project management techniques to shorten time to market, enhance their ROI and product risk management and improve product quality, efficiency and customer satisfaction.
Such is the impact of Agile that Digital.ai’s 15th State of Agile Report found that its adoption by software development teams increased from 37 per cent to 86 per cent in just a year. While 64 per cent of respondents to Digital.ai’s survey said that Agile helped enhance their ability to manage changing priorities and accelerate software delivery, 47 per cent said the methodology enhanced team productivity and improved alignment between business and IT teams.
But at what cost?
Organisations have transformed their product development and delivery processes rapidly, but many have neglected to integrate robust security into their development processes. Not scanning products or applications for security failures can have wide-ranging consequences. For instance, 33 vulnerabilities found in seven open source “TCP/IP stacks” exposed millions of embedded devices to attacks such as information interception, denial of service and total takeover. These devices included smart home sensors and lights, barcode readers, enterprise network equipment, building automation systems, and even industrial control equipment.
Cyber-physical systems protection company Claroty’s the State of XIoT Security Report: 1H 2022, found that vulnerability disclosures impacting IoT devices increased by 57 per cent in the first half of 2022 compared with the previous six months, with the combination of IoT and IoMT (Internet of Medical Things) vulnerabilities (18.2 per cent) exceeded IT vulnerabilities (16.5 per cent). The report revealed that 71 per cent of these vulnerabilities impacted system and device availability, 54 per cent enabled remote code or command execution, and 43 per cent enabled denial-of-service conditions (crash, exit, or restart).
Why is it so difficult to secure today’s products and applications?
Sarit Tager, VP Product at JFrog Security, says that there are a variety of factors that make it difficult to achieve comprehensive security for products delivered and deployed by organisations. “A key one is the growing the volume, variety and complexity of software and connected devices in use. Another is the overwhelming risk of inherited software supply chain exposures,” he says. “The result: companies struggle every day to provide software with optimal security and protection against malicious activities, takeovers, data theft, and commercial sabotage.”
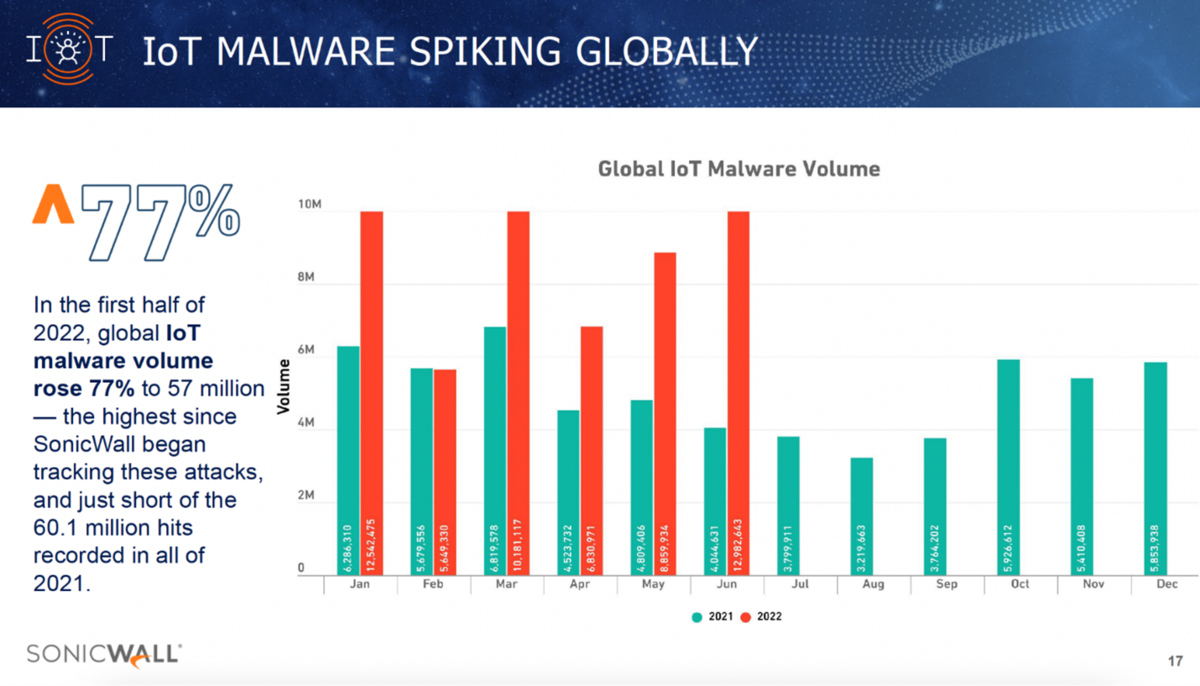
Combining these factors with the avalanche of cyber-attacks on connected devices makes the challenge even more insurmountable. According to SonicWall, the total number of malware attacks on IoT-enabled devices rose by 77 per cent in the first half of 2022 to an alarming 57 million. The number of “never-before-seen” malware variants, that are the hardest to defend against, also rose by 45 per cent in the period.
In 2021, as many as 97 per cent of UK organisations suffered a supply chain breach, compared with 82 per cent that suffered the same fate in 2020. These figures indicate that despite advancements in product development and delivery, today’s digital products and applications are vulnerable to a variety of cyber-security threats, primarily due to the inability of manufacturers to integrate robust security into their development processes.
Tager says that securing products during their entire lifecycle should be the topmost priority for organisations. In the development phase, every piece of code should be tested for vulnerabilities and a gatekeeping mechanism should be in place to ensure that products or software are shipped with no exploitable issues.
See More: Cyber security and digital transformation: getting it right from the start
Are governments and organisations doing enough to turn the tide?
The vast variety of cyber-security threats faced by billions of connected devices deployed worldwide paints a sorry picture of organisations’ cyber-preparedness. But are they aware of the dangers that lie ahead? A study by Synopsys found that not only are a vast majority of organisations aware of the threat, they are actively taking steps to ensure the security of their products and software supply chains.
The company’s BSIMM13 Trends & Insights report, based on an analysis of software security practices of 130 global organisations, revealed that 90 per cent of the organisations in the BSIMM13 data pool have established software security checkpoints in their software development lifecycles (SDLCs), and 82 per cent use automated code review tools that allow them to perform faster, incremental security tests and identify vulnerabilities as they are introduced throughout the SDLC.
Jason Schmitt, general manager of the Synopsys Software Integrity Group, said that this risk-based approach to application security “recognises that security isn’t limited to the codebase; it includes the process of software development where security reviews and testing ‘shift everywhere’ to continuously improve security outcomes.”
The winds of change are here
The PSA Certified 2022 Security Report, aptly named ‘The Turning Point for IoT Security – 2022: The Year of Change’ based on a survey of 1,038 technology decision makers across Europe, USA, and APAC, has also revealed encouraging developments concerning the prioritisation of the security of connected devices.
As many as 90 per cent of those surveyed said they witnessed security increase in importance over the past 12 months, a trend influenced by customers prioritising checking for security in connected devices. 96 per cent said they would be interested in an industry-led set of guidelines on IoT best practices, and 90 per cent said security is among the top three priorities for their business. These factors indicate changing priorities brought about by changing customer demands, a trend backed by the fact that 96 per cent of ITDMs believe having security in their products positively impacts their bottom line.
“Where application security was once an afterthought, something to be addressed after market share was secured, creating a security-first culture is now the new business mantra,” said Tim Mackey, principal security strategist at the Synopsys Cybersecurity Research Centre. “That’s partly a recognition that business risk stems from unmitigated software risks. With software entering businesses from multiple sources, many of which are associated with hardware like an IoT device, lapses in IoT security can have a material impact on the risk profile for the business.”
Bringing connected devices under the law
Be it President Biden’s Executive Order on Improving the Nation’s Cybersecurity, the European Union’s EU Cyber Resilience Act, or the UK’s Product Security and Telecommunications Infrastructure Bill (PSTI), many countries are now introducing and enacting new legislation to make the security of connected devices the foremost priority for manufacturers and sellers.
For example, the UK’s Product Security and Telecommunications Infrastructure Bill, which is awaiting royal assent, was introduced to prevent the sale of consumer connectable products in the UK that do not meet baseline security requirements and – to get the point across – introduce fines of up to £10 million or up to 4 per cent of global revenue, whichever is greater, for firms failing to comply.
The EU Cyber Resiliency Act, published in September this year, is also a step towards ensuring strong cyber-security standards for hardware and software products. The legislation ensures that manufacturers ensure the security of products during the design and development phase and throughout the product life-cycle, enhance the transparency of security properties of products, and enable businesses and consumers to use digital products securely.
The bottom line: transparency is critical
Organisations’ increasing awareness of cyber-security threats impacting hardware and software products deployed or delivered by them, combined with increasing legal scrutiny of manufacturers’ intent to secure their digital products, represents a sea change from the time when connected device security suffered from government apathy and sellers’ need to rush products to the market as quickly as they could.
We are still a long way from making every connected device secure, but the first steps have been taken. Joseph Carson, Chief Security Scientist at Thycotic, said that the new UK law to improve security on smart devices is a welcome step in the right direction, but that it must go further to ensure that it includes security best practices that are part of the solution.
“Transparency is critical, so when purchasing a new smart device, it MUST be clear on how long the vendor continues to provide security updates, just like a manufacturer warranty period or an expiration date. This type of approach will provide consumers with a clear choice when choosing smart devices comparing one vendor that only provides two years of security updates versus another that will provide five years,” Carson said.

Business Reporter Team
Most Viewed
Winston House, 3rd Floor, Units 306-309, 2-4 Dollis Park, London, N3 1HF
23-29 Hendon Lane, London, N3 1RT
020 8349 4363
© 2025, Lyonsdown Limited. Business Reporter® is a registered trademark of Lyonsdown Ltd. VAT registration number: 830519543





